- Decrypt Keychain.plist Password
- Decrypt Keychain.plist Codes
- Decrypt Keychain.plist Email
- Decrypt Keychain.plist File
- Decrypt Keychain-backup.plist
In iTunes backup, the iPhone Keychain sqlite database is stored as a Plist file. The Keychain file gets stored with 51a4616e576dd33cd2abadfea874eb8ff246bf0e file name in the iTunes backup folder.
Here is the command to covert cryptic 'keychain.plist' file to easily readable 'keychain.xml' file. Plutil.exe -convert xml1 -s -o c:keychain.xml 'c:usersadministratorappdataroam ingapple computerpreferenceskeychain.plist' This is how it will look like after decoding to XML file. Internals of Safari Encryption Algorithm.
Keychain data stored in the backup is encrypted using a hardware generated key – key 0x835. So renaming the file 51a4616e576dd33cd2abadfea874eb8ff246bf0e to keychain-backup.plist and editing with a plist editor opens the file but does not display the data in it.
5. Install python dependencies.
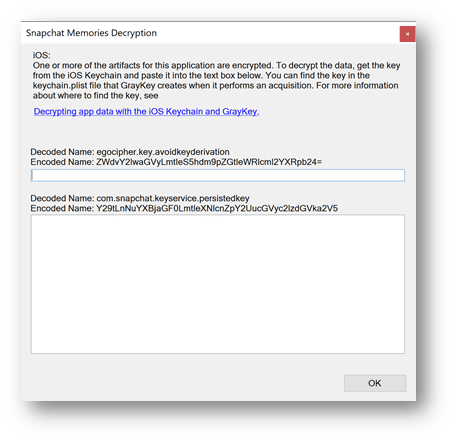
- Computerworld covers a range of technology topics, with a focus on these core areas of IT: Windows, Mobile, Apple/enterprise, Office and productivity suites, collaboration, web browsers.
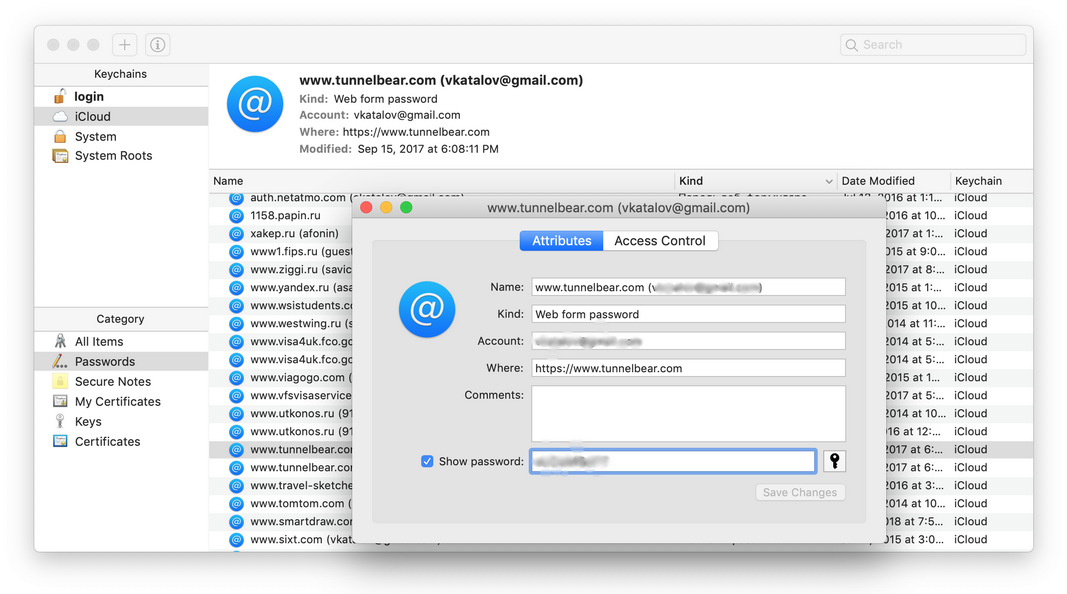
- Keychain encrypts the stored passwords and credit card numbers with 256-bit AES, which is one of the most advanced encryption standards available. The facility also employs end-to-end encryption tech and works to provide a device with a unique key and passcode. Only the user is supposed to know the passcode used to access keychain.
Decrypt Keychain.plist Password
6. Navigate to iphone-dataprotection folder and run keychain_tool.py by supplying keychain-backup.plist path and the backup folder path.
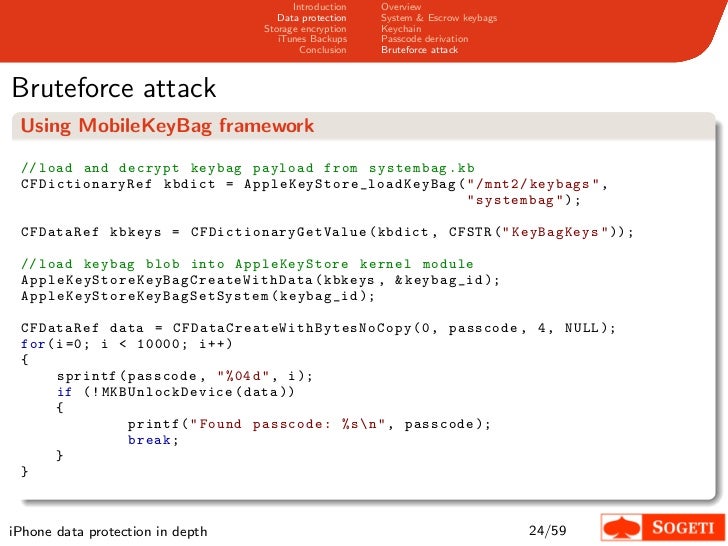
 7. The script prompts for key 0x835. key in the value obtained in step 2. keychain-tool.py automatically decrypts the backup keychain content and displays it on the terminal.
7. The script prompts for key 0x835. key in the value obtained in step 2. keychain-tool.py automatically decrypts the backup keychain content and displays it on the terminal.
2. Rename the file 51a4616e576dd33cd2abadfea874eb8ff246bf0e to keychain-backup.plist.
3. Extract key 0x835 by following my previous blog post – Extracting AES keys from iPhone.
4. Download & install mercurial. Researchers at sogeti developed tools to decrypt the keychain files. Grab the tools by running the below command from windows command prompt. It creates iphone-dataprotection folder in the current directory.
5. Download and install Python 2.6 in C:Python26 folder.
6. Add C:Python26 to system PATH environment variable.
7. Install windows openSSL.
8. Install python dependencies – setuptools, M2Crypto, pycrypto & pyqt
9. Download progressbar-2.3.rar and extract it to c: drive. From command prompt navigate to c:progressbar-2.3 and type the below command.
10. Download construct-2.06.rar and extract it to c: drive. From command prompt navigate to c:construct-2.06 folder and type the below command.
11. From command prompt, navigate to iphone-dataprotection folder and run keychain_tool.py by supplying keychain-backup.plist path and the backup folder path.

* In the above command replace [user name] & [UDID] with appropriate values.
12. The script prompts for key 0x835. key in the value obtained in step 2. keychain-tool.py automatically decrypts the backup keychain content and displays it on the command prompt.
More detailed video demonstration is available at – iPhone forensics – Analysis of iOS 5 backups: video.
For iOS 7, apply this patch – https://code.google.com/p/iphone-dataprotection/issues/detail?id=115
Share this:
Decrypt Keychain.plist Codes
Posted by satishb3 on May 3, 2012 in iPhone
Decrypt Keychain.plist Email
A PLIST file is a settings file used on Apple operating systems, also known as 'Property List' file. PLIST file is widely used by iOS apps and macOS applications. macOS provides several ways to open and view PLIST file, for example xcode and 'Property List Editor'. But there is no such program to view plist file on windows. iBackup Viewer offers a free utility tool to view binary and xml PLIST files, also provides a simple HEX viewer to view binary data value of the plist file. Please follow these steps to open plist file on Windows.
Decrypt Keychain.plist File
Install and Launch iBackup Viewer
Download and install iBackup Viewer on your computer, launch iBackup Viewer.
Open Property List Viewer
When iBackup Viewer starts, choose 'Property List Viewer' from the main menu
Click the 'Open' button to open and view a PLIST file.
iBackup Viewer supports editing property list file starting from version 4.18.2 (4.1820 for Mac)Change type of item
Allow editing value of plist item
Easily undo or redo changes
To view binary data value looks like '<6400a322 f303ac23....a3c4d232>', double click on the value to open hex viewer.Edit value of 'Data' item
iBackup Viewer supports pasting base 64 string to edit value by pressing Control + V or Command + V when 'Data' item is selected.